As a unit of Information Technology, the mission of IT Security Services is to protect the confidentiality, integrity, and availability of the University's information assets.
To accomplish this mission, we leverage a variety of technological and human resources, and work with other IT units and customers across the University. We also assist with cybersecurity-related inquiries and investigations and provide documentation available in the form of Knowledge Base articles.
If you suspect a system has been compromised, please take the following steps:
- Do not attempt to investigate the incident yourself.
- Do not power off the computer.
- Immediately stop working on the system and do not open or close any applications.
- Disconnect the computer from the network by
- unplugging the network cable or
- disabling the wireless adapter.
- Using a different computer, report the incident using the link above or via phone.
Contact Us
View and request services or browse for quick answers.
Daytona Beach Campus
386-226-6990
Prescott Campus
928-777-6990
Worldwide Campus
Toll Free: 866-227-8325
Outside USA: +1-386-226-6990
Common Support Topics
Passwords
Help with Cybersecurity
Resources
- Guidelines for Computer Use While Traveling
- What is Phishing?
- Security Awareness Training
- Sending Encrypted Email
- What is Two-Factor Authentication?
- What is Device Encryption?
- Worldwide - Get Application Whitelisting Client
- Remote Access to University Network Using VPN
- What Policies & Laws affect me?
- What Policies & Laws Should I Be Concerned With?
Security Phish Tank
The information below highlights examples of actual phishing attacks that have targeted Embry-Riddle. These examples are provided to help improve awareness of phishing attacks and to provide education on how to spot a phishing attack.
Phishing attacks change constantly, so not every possible phishing email will be shown in the examples below.
If you receive an email that seems suspicious, please report it using the Phish Alert button in Outlook.
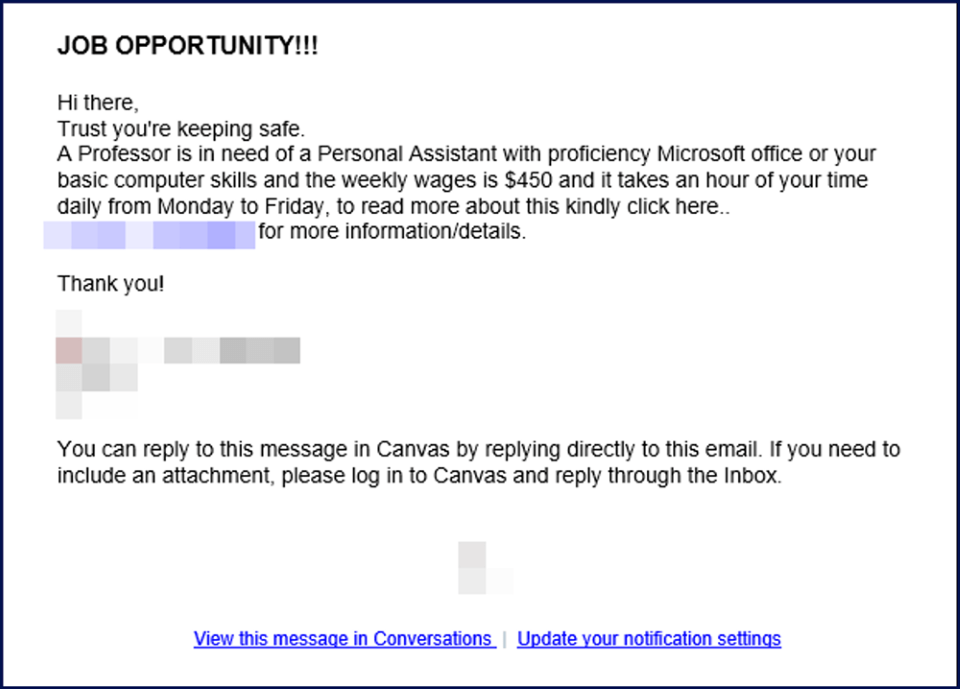
One phish that has been seen more frequently in recent is related to job offers to be personal assistants for professors. The example seen here was triggered through a message in Canvas that also generates an email to the recipient. A student account in Canvas was compromised and the attacker used that access to target other students.
The phishing email frequently does not have an attachment or even a link but asks for contact information to be sent to an email address. After responding, the attacker may use other forms of communication such as texting. Eventually the scammer will ask for some sort of financial action, which might be gift card purchases, or the attacker sends a check and then asks for funds to be wired back to the attacker. The check is invalid, and the victim is left responsible for the funds transfer.
Any employment offers from ERAU will originate from our Workday system. Anything outside that channel is a scam.
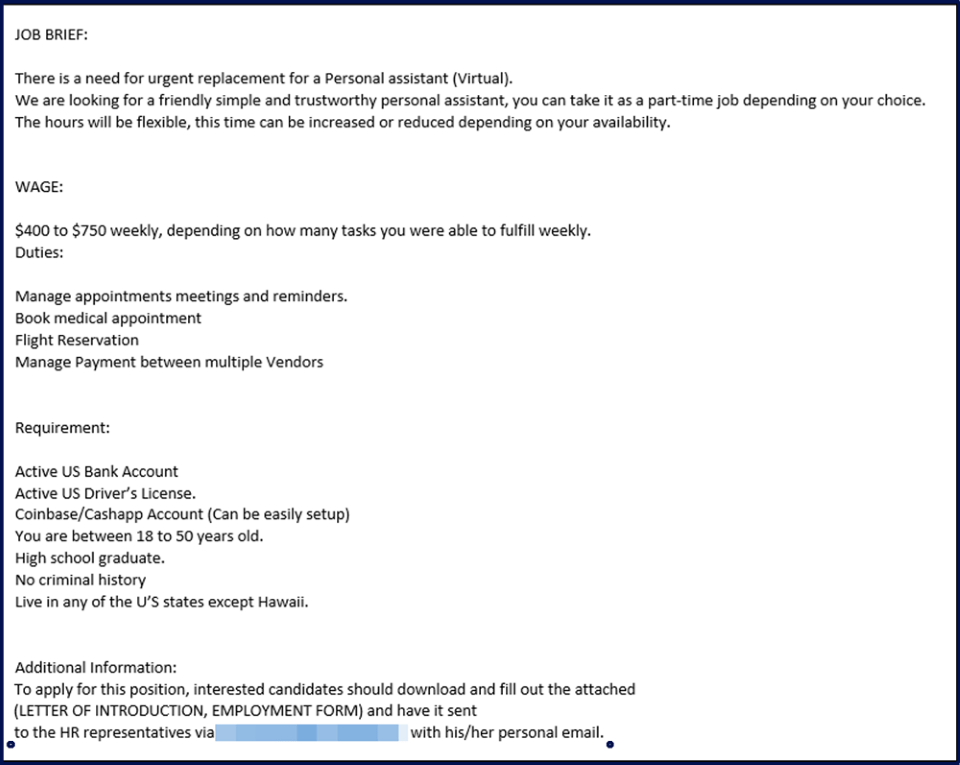
There are have been multiple phishing attempts related to job offers to be virtual personal assistants. This example had multiple attachments and requested specific banking information in addition to some basic personal information.
For this campaign, the initial contact was via email but then would shift to other forms of communication such as texting. This campaign also seemed more focused on the potential use of Cryptocurrencies.
Any employment offers from ERAU will originate from our Workday system. Anything outside that channel is a scam.
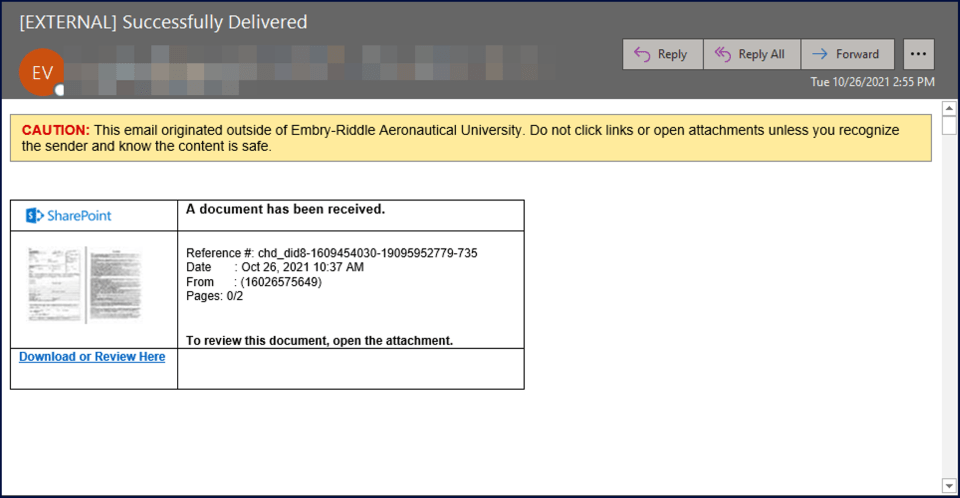
This type of phish takes advantage of the widespread use of services such as Microsoft 365. A notification is sent that a document is available on the service and asks for the recipient to click on the link to the document. This can be challenging to identify as phishing since we do receive documents from many sources and we will not always know in advance that it will be sent.
Holding the cursor over the link reveals that this document in not hosted in SharePoint online or in the Microsoft environment, so that remains a useful technique to determine if the document is consistent with what it claims to be and where it can be accessed.
Use caution when accessing links from outside senders, especially when the messages are not expected or originate from unknown sources.
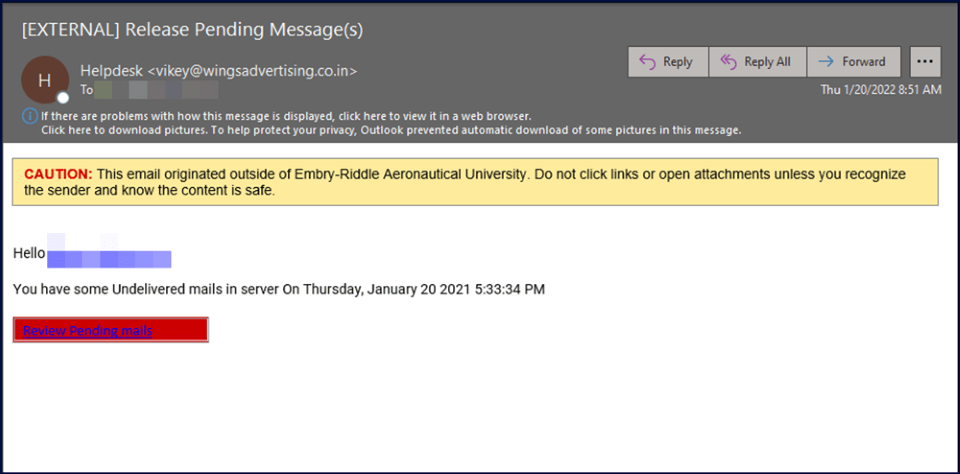
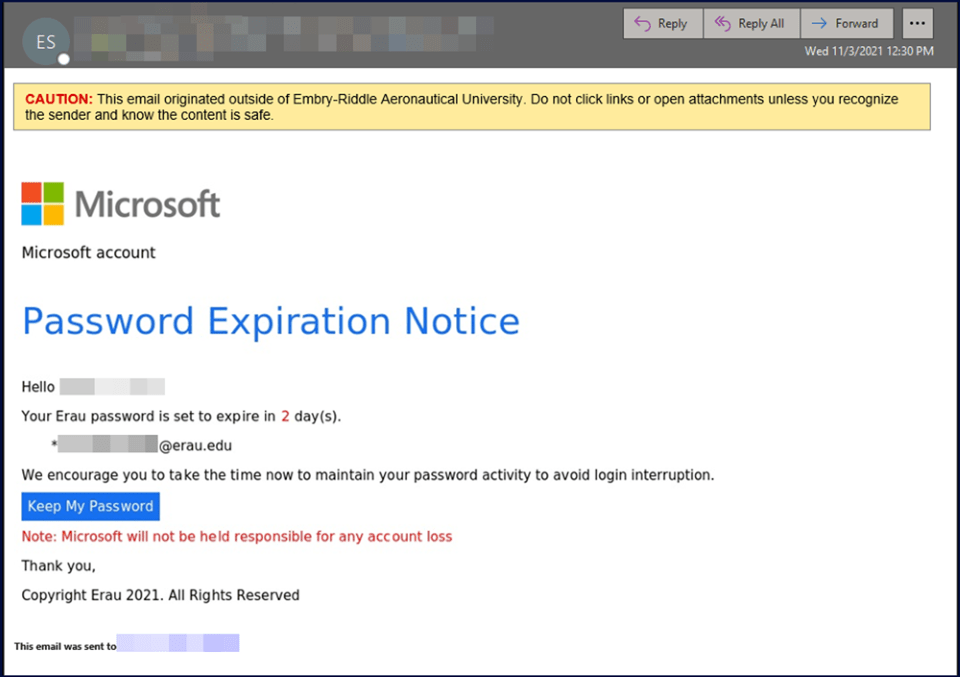
This is one of the most common types of phishing attacks. The attacker is trying to steal credentials from valid users by creating a sense of urgency related to account issues. The link is likely to take the victim to a page that may look exactly like the usual Microsoft 365 login page or even like the ERAU single sign-on page.
The page will collect the username and password and can either display an error message after collecting the data or redirect to another page to make it appear that the problem has been solved.
ERAU IT staff will NEVER ask for your password. Password expiration notices will pop up during the normal login process and are not sent via email.
Modern mail systems often have a spam quarantine feature where messages identified as spam are held by the system rather than being delivered to the recipient.
This quarantine feature allows review and release of messages that may have been improperly marked as spam. This example of a phishing attack tries to use the idea of a quarantined message as a method to get the victim to click on the link.